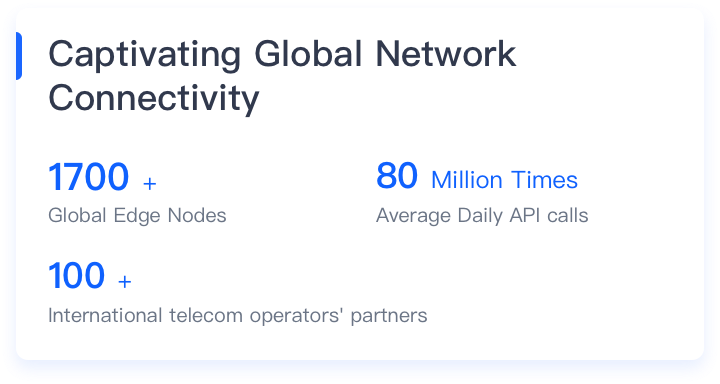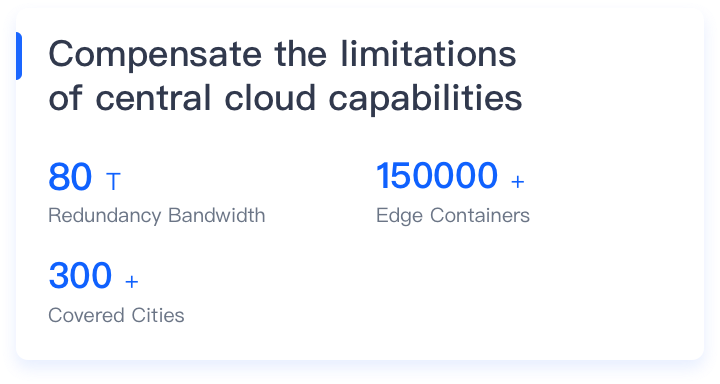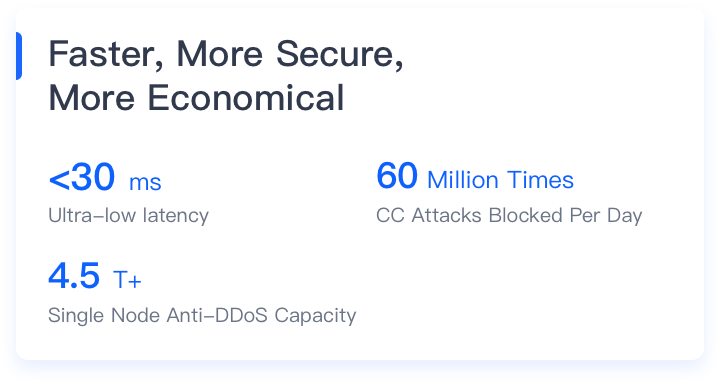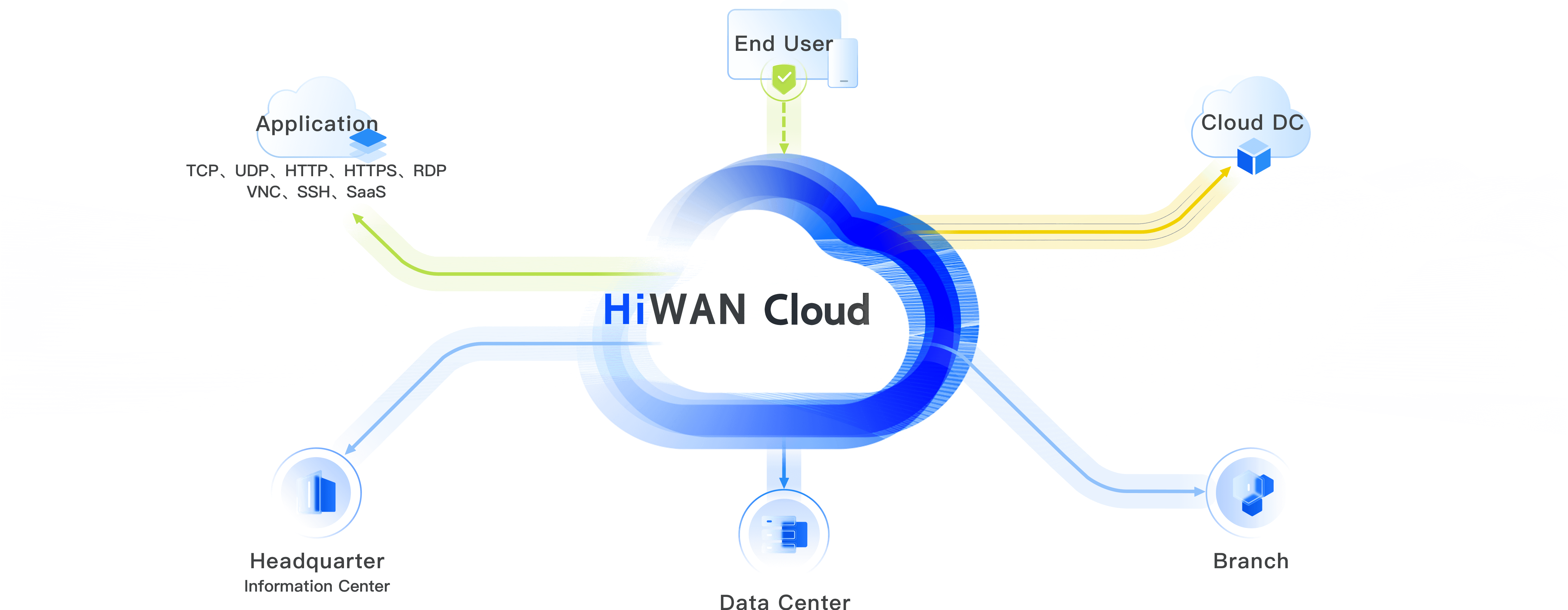









Economical Edge Cloud Products



- Edge whole site acceleration network
- Edge download delivery network
- Edge streaming delivery network
- Edge global application acceleration
- Edge global link acceleration
- Cloud WAF
- Anti-DDoS
- Edge security acceleration
- Advanced Threat Detection (ATD)
- Firewall
- Hide asset exposure surface
- Unified identity management
- Endpoint baseline detection
- Advanced threat defense
- Fine-grained authorization
- Security visualization
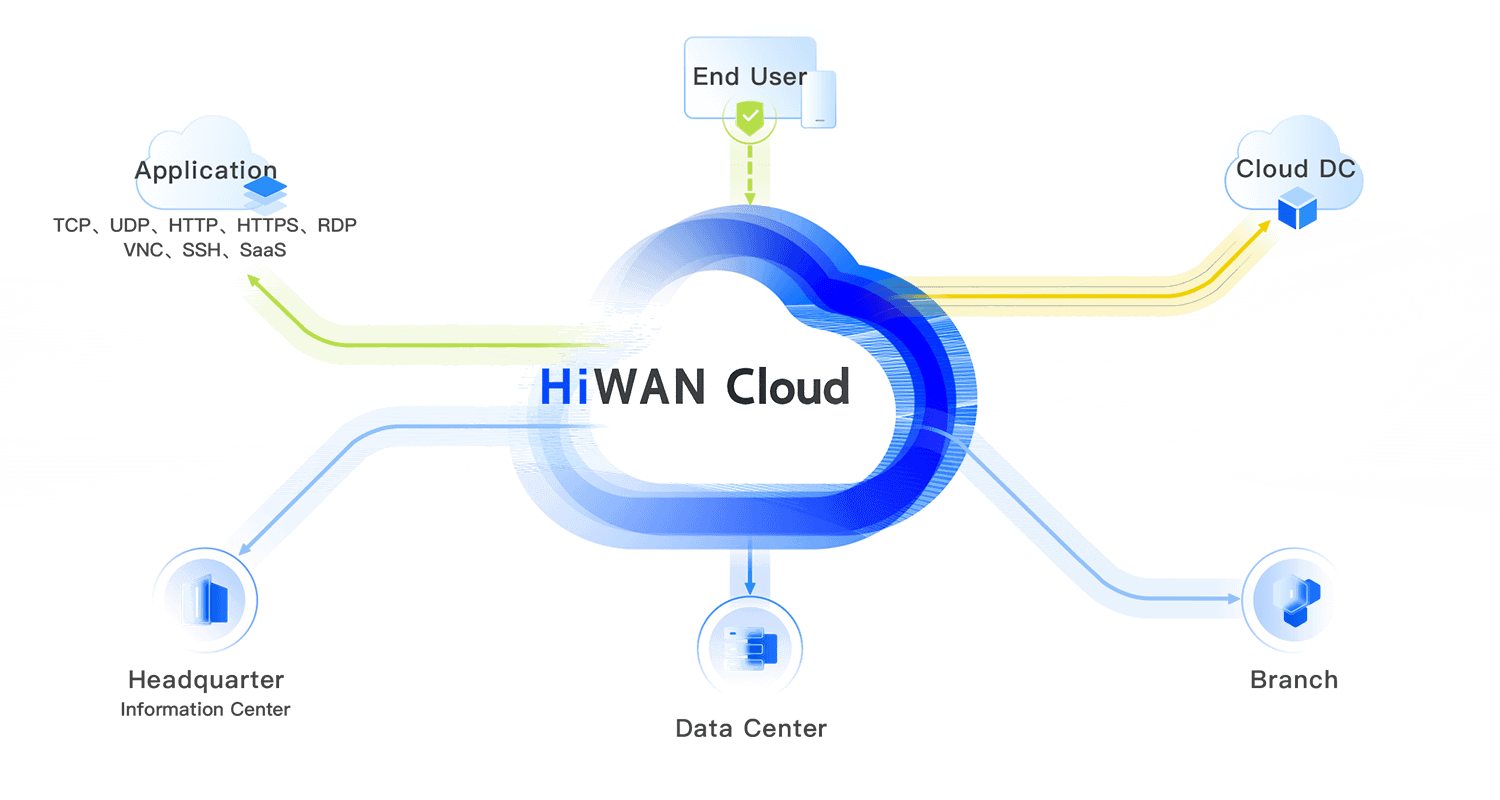
- Intelligent routing
- WAN transmission optimization
- Cloud-based unified management
- Security defense system
- Edge cloud server
- Edge container
- Bare metal cloud
- Serverless
- Orchsym iPaaS

- Global Content Delivery
- Portal Website Edge Security Acceleration
- Global Link Acceleration
- Enterprise Security Networking & Zero Trust Access Acceleration
- API Management& Security Protection
- Global Edge Computing Distribution